Precise detection, classification, and contextualization of vulnerabilities, enriched with vulnerability intelligence to support effective prioritization. By leveraging real-time threat intelligence, we identify which vulnerabilities are actively exploited or targeted by specific threat actors. This, combined with prioritized remediation strategies, ensures full visibility into your security and compliance posture, empowering you to safeguard your assets precisely and confidently.
Vulnerability Management (VMaaS)
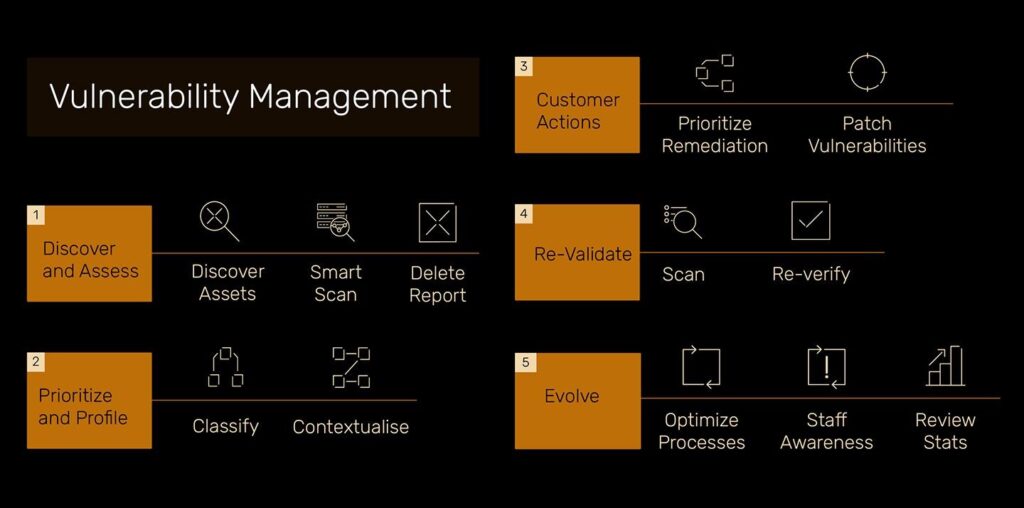
Detect, classify, and contextualize vulnerabilities, with designed and prioritized remediation programs.
What Does Vulnerability Management as a Service Do?
Scanning
Generate detailed reports identifying security weaknesses across systems, applications, and networks.
Prioritization
Vulnerabilities are prioritized based on severity and impact, with actionable remediation steps provided for addressing critical issues.
Reporting
Ongoing trend analysis and reports ensure the organization’s vulnerability landscape is monitored and aligned with regulatory compliance standards.
Benefits of Vulnerability Management as a Service
Accurate Prioritization
By identifying key areas of concern, therefore reducing recovery time for remediation.
Round-the-clock
Support for scheduling, monitoring, analysis, and reporting of scanning activities.
Identify and Map
Your business risk level to cyber threats.
Remediation Reports
Monthly prioritized remediation report, and access to Threat Intel Advisories.
Visibility
Visibility to stakeholders by highlighting your business’s attitude towards cyber security.
Realize ROI
By unleashing the full potential of your technology investments by maintaining a healthy cyber security posture.
Organizations using VMaaS saw a 40% reduction in their overall attack surface.
SOURCE: Forrester
Differentiators
Enrichment of Vulnerabilities
With Threat Intelligence data.
Auditable Collaboration
Precise and applicable synopsis, and carefully crafted reports.
Dedicated Vulnerability Management Team
Available 24/7.
MA3 Cyber Response Platform
The MA3 Cyber Response Platform enhances collaboration by pre-empting, identifying, and mitigating risks before they become security incidents.
