Network Detection & Response involves the continuous monitoring and analysis of your networks to detect and respond to threats, including malware, data exfiltration, and intrusions. By partnering with SecurityHQ, we leverage your technologies to ensure a secure environment for your events, protecting both participants and sensitive information.
Key Benefits
Risk Reduction
Reduce attack surface and maximize the ROI of your existing cyber security technologies.
Complete Visibility
SHQ Response Platform allows you to visualize, prioritize, escalate and respond to incidents.
Expert Team
450+ security experts, threat hunters, and SANS GIAC certified Incident handlers and forensic analysts.
What Does Network Detection & Response Do?
24/7 Triage
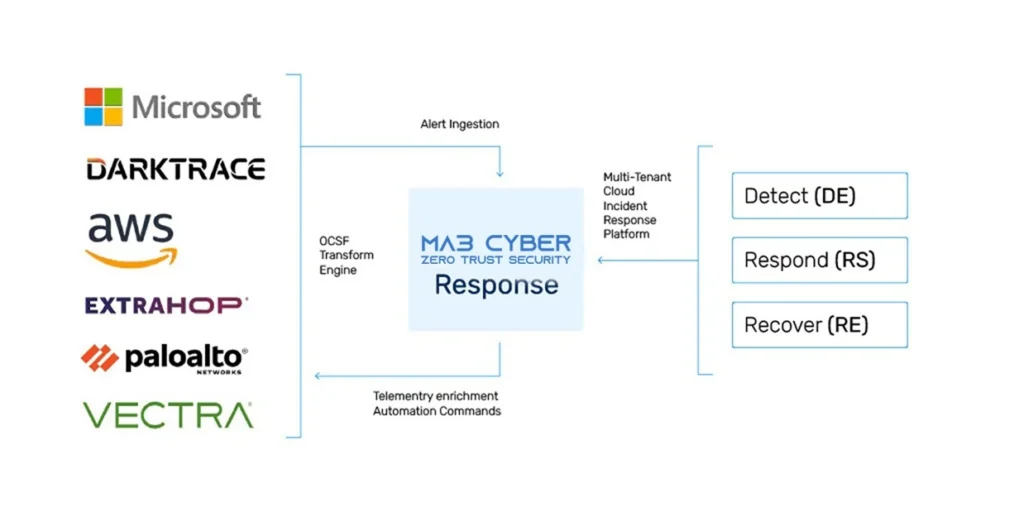
MA3 Cyber ingests and normalizes alert data, then enriches detections with additional network event data to qualify the alerts to improve fidelity and reduce noise. Playbook automation ensures triage analysis in seconds.
24/7 Investigation
Network packet and event data are investigated to determine impact by identifying the alert, gathering evidence, analyzing logic, using advanced search, correlating activities, performing packet capture, and reviewing findings.
24/7 Eradication
Malicious payloads and artifacts identified during the investigation stage are cleaned and eradicated.
Tuning
Analysts perform model tuning by adjusting parameters, adding or removing criteria, and setting anomaly scores. Test the changes, monitor real-time data, and iterate to ensure accurate threat detection and minimal false positives.
Benefits of Securing Networks
Activity Analysis
Anomalous network behavior using both supervised and unsupervised learning is prone to high noise and false positives. MA3 Cyber improves the credibility of detection events with continuous tuning.
Immediate Response
76% of ransomware attacks occur outside of business hours, with 49% happening during night-time on weekdays and 27% over the weekend. 24/7 rapid Detection & Response is critical.
Correlation
The confidence and impact of NDR alerts are corroborated with multi-source correlation across endpoint, firewall, domain controller, and host logs.
Domain Expertise
Modern networks are complex, with diverse traffic types and protocols. Analyzing this variety requires deep expertise and sophisticated tools to accurately interpret the data.
Azure and AWS Cloud
MA3 Cyber can correlate AWS VPC flow logs and Azure Virtual Network for threat detection, providing visibility into unusual patterns, and detecting unauthorized access and data exfiltration.
Smart Automation
Central support for automation of repetitive processes. Increased accuracy and shortened recovery time for remediation.
23% of data breaches involved network intrusion, with many breaches stemming from weaknesses in network security.
SOURCE: Verizon
How MA3 Cyber is Different
Agnostic threat management and reduced exposure.
Adversary Exposure Mitigation (AEM)
MA3 Cyber AEM program leverages Network Detection & Response to target weaknesses and compliance issues such as legacy protocols, weak encryption, and lack of network segregation.
Surface Unknown Unknowns
MA3 Cyber mitigates the risk of threats or vulnerabilities that are unforeseen and undetected by current security measures. Machine learning baselining helps detect novel threats by continuously learning and adapting to normal network behavior, enabling the identification of subtle anomalies that traditional methods might miss.
Bring Your Technology
MA3 Cyber has expertise in leading NDR, and provides and orchestrates analytics of AWS and Azure network analytics.
Cloud Threats
Cloud-native deployments are susceptible to attacks via exploitation of web vulnerabilities, malicious or vulnerable applications, misconfigurations in the virtual networking stack, and weak access controls. Once compromised, cloud environments are often susceptible to lateral movement and exfiltration. MA3 Cyber focuses on cloud environments which are typically overlooked.
MA3 Cyber Response Platform
MA3 Cyber Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
