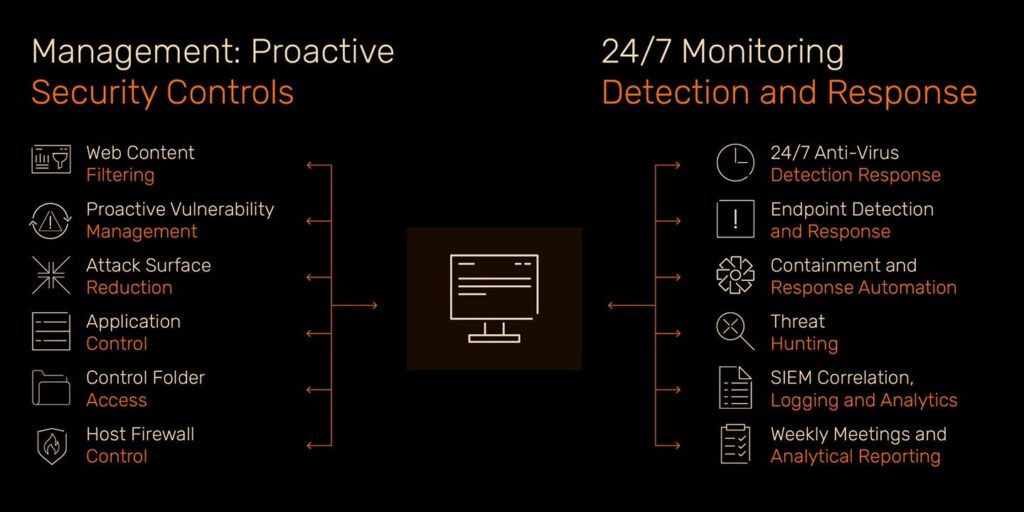
Endpoint and end-user devices such as servers, desktops, and laptops on any network can be exposed to exploits, misuse, and malicious actors. Preventative controls are by far the best strategy. But this requires configuration and maintenance by skilled engineers.
Our team provides proactive administration services to deliver complete visibility of all your endpoints. Monitor all communications, from low-level activity to malicious threats, and identify and respond to all elements targeting your endpoints.