Identifying and classifying sensitive data, then configuring DLP solutions to work effectively within complex environments, can be overwhelming. Traditional solutions often struggle with accuracy — generating false positives that cause alert fatigue and false negatives that allow breaches to slip through. MA3 Cyber’s Data Detection & Response (DDR) solution is built to overcome these challenges, delivering accurate, adaptive data protection without the noise.
Data Detection & Response
Protect Your Data with Intelligent MXDR Response
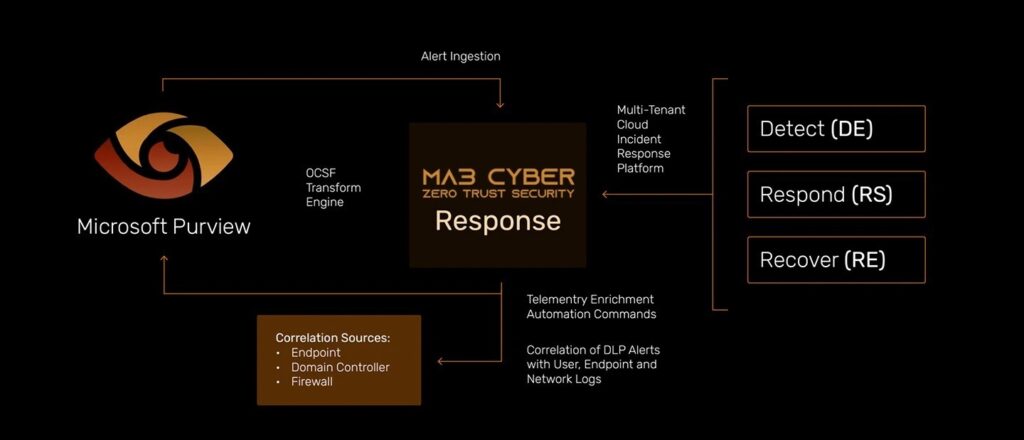
MA3 Cyber’s Data Detection & Response Service, powered by Microsoft Purview, is designed to enhance data security through 24/7 monitoring, detection, and rapid response.
Key Benefits
Minimized Risk
Reduce exposure to threats and maximize the value of your current security technologies.
End-to-End Visibility
The MA3 Cyber Response Platform empowers you to visualize, prioritize, escalate, and resolve incidents with precision.
Trusted Experts
Backed by 450+ experts — from threat hunters to SANS GIAC–certified incident handlers and forensic analysts.
What Does Data Detection & Response Do?
Investigation
- Quarantine File: Isolates a suspicious file to prevent further access or spread.
- Block User: Temporarily restrict a user’s access to prevent further malicious activity.
- Reset Password: Force a password change for a potentially compromised account.
Revoke Access
- Remove Document Sharing: Revoke sharing permissions on sensitive documents.
- Apply Sensitivity Label: Add a label to classify and protect sensitive data.
- Disable Account: Deactivate a user account to stop ongoing malicious actions.
- Isolate Device: Disconnect a device from the network to prevent further data.
Triage in Seconds
- Activity Monitoring to continuously track data.
- Track access and movement.
- Track policy violation alerts.
Benefits of Data Detection & Response
Data Breach Reduction
Organizations with well-implemented Data Loss Prevention solutions report a significant reduction in breaches.
Multi-Source Correlation
The confidence and impact of DDR alerts are corroborated with multi-source correlation across endpoint, firewall, domain controller, and host logs.
Compliance Reporting
MA3 Cyber supports compliance reporting against regulations and frameworks such as GDPR, HIPPA, and DORA.
Detect Insider Threats
Insider threats are often the hardest to detect. Our data solutions help monitor user behavior and prevent malicious actions before they result in a significant data breach.
Detection systems helped organizations save an average of $2 million on the total cost of a data breach
SOURCE: IBM
Differentiators
Agnostic threat management and reduced exposure.
MA3 Cyber provides Governance consulting on policy, together with Protective Controls Management to apply rules and policies. The DDR service integrates across those services to provide end-to-end support.
Data Security Ecosystem
Managed Risk
Managed Data Governance MA3 Cyber Managed Risk. Consulting on policy and data categorization. Assists in meeting data protection regulations like GDPR and HIPAA.
Managed Protect
Managed Data Protection implementing rules to restrict data access based on user roles and data sensitivity.
Managed Detect
Managed Data Detect & Respond Detect and respond to data-related security threats in real-time.
