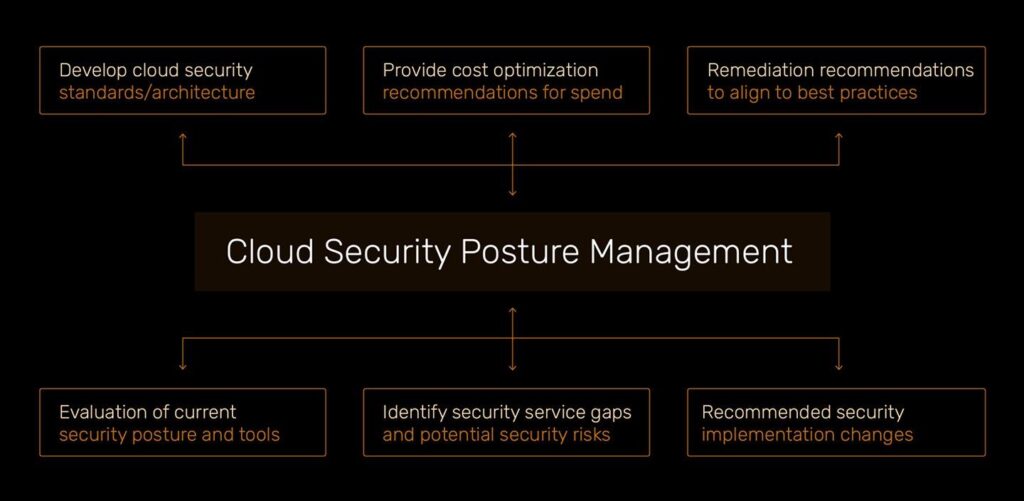
Continuously monitor and analyze cloud environments to identify misconfigurations, vulnerabilities, and compliance risks. Enforce security best practices by detecting and remediating issues in cloud infrastructure, ensuring that configurations align with regulatory standards and security policies.
Cloud Security Posture Management (CSPM)
Monitor and manage cloud security configurations to ensure compliance with best practices and regulations.
What Does Cloud Security Posture Management Do?
Continuous Security Monitoring
Scan cloud environments for misconfigurations, vulnerabilities, and security risks.
Automated Remediation
Automatically fix security issues and misconfigurations to maintain a secure cloud posture.
Compliance Enforcement
Ensure cloud configurations align with regulatory and industry compliance standards.
Benefits of Cloud Security Posture Management
Automated Compliance
Continuous compliance with industry standards and regulations.
Improved Security Visibility
Clear visibility into cloud security risks and misconfigurations.
Reduce Financial Impact
Minimize financial impact from security incidents and inefficiencies.
Enhanced Incident Response
Speeds up detection and response to cloud security threats.
Monitoring and Remediation
Real-time detection and fixing of security issues.
Data Breach Risk Reduction
Reduces the risk of data breaches and unauthorized access through proactive monitoring.
Over 60% of cloud breaches are attributed to misconfigurations.
SOURCE: Gartner
Differentiators
Focus on Cloud-Specific Configurations and Vulnerabilities
Identify cloud-specific misconfigurations and vulnerabilities, while traditional security services focus on on-premise threats.
Compliance and Governance
Ensure cloud compliance with regulations like GDPR and HIPAA, while other services are less focused on cloud-specific standards.
Cloud-Native and Dynamic Nature
Monitor dynamic cloud environments in real-time, unlike traditional tools that aren’t suited for rapid cloud resource changes.
Proactive Risk Identification
Detect misconfigurations and risks before they are exploited, whereas other services mainly detect ongoing threats.
